Enterprises are running their workloads across complex, hybrid infrastructures, and need solutions that provide full-stack, 360-degree visibility to support rapid time to identify and resolve security threats. Trend Micro Deep Security offers seamless integration with Sumo Logic’s data analytics service to enable rich analysis, visualizations and reporting of critical security and system data. This enables an actionable, single view across all elements in an environment.
I. SOLUTION COMPONENTS FOR INTEGRATION

DEEP SECURITY MANAGER (DSM)
This is the management component of the system and is responsible for sending rules and security settings to the Deep Security Agents. The DSM is controlled using the web-based management console. Using the console, the administrator can define security policies, manage deployed agents, query status of various managed instances, etc. The integration with Sumo Logic is done using this interface and no additional component or software is required.
DEEP SECURITY AGENT (DSA)
This component provides for all protection functionality. The nature of protection depends on the rules and security settings that each DSA receives from the Deep Security Manager. Additionally, the DSA sends a regular heartbeat to the DSM, and pushes event logs and other data points about the instance being protected to the DSM.
SUMO LOGIC INSTALLED COLLECTORS AND SOURCES
Sumo Logic Installed Collectors receive data from one or more Sources. Collectors collect raw log data, compress it, encrypt it, and send it to the Sumo Logic, in real time via HTTPS. The Deep Security Solution Components forward security events to Installed Collectors with a syslog source.
SUMO LOGIC DATA ANALYTICS SERVICE AND WEB UI
The Sumo Logic Web UI is browser-based and provides visibility and analysis of log data and security events sent by the Deep Security Platform to the Sumo Logic service and also provides administration tools for checking system status, managing your deployment, controlling user access and managing Collectors.
 SUMO LOGIC APP FOR TREND MICRO DEEP SECURITY
SUMO LOGIC APP FOR TREND MICRO DEEP SECURITY
The Sumo Logic App for Trend Micro Deep Security delivers out-of-the-box Dashboards, saved searches, and field extraction for for each security module in the Deep Security solution, including Anti-malware, Web Reputation, Intrusion Prevention, Host-based Firewall and File Integrity Monitoring.
II. HOW THE DEEP SECURITY INTEGRATED SOLUTION WORKS
Overview
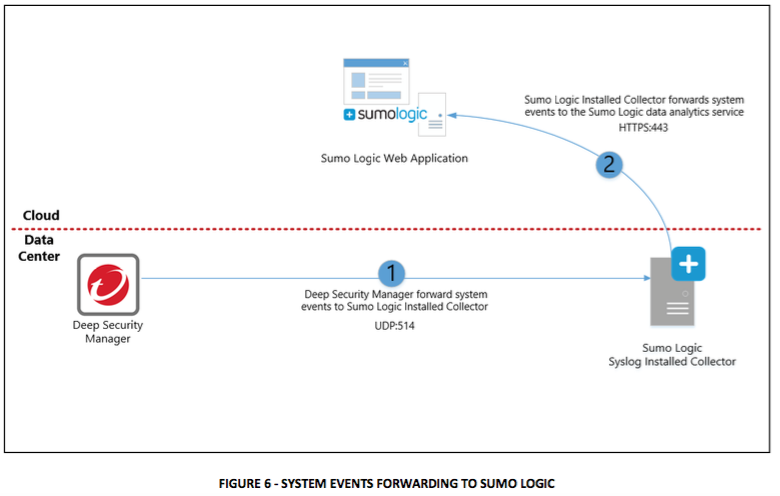
Trend Micro Deep Security Software and Deep Security as a Service integrates with Sumo Logic through the Installed Collector and Syslog Source. This Syslog Source operates like a syslog server listening on the designated port to receive syslog messages from Trend Micro Deep Security Solution. The Installed Collectors can be deployed in your environment either on a local machine, a dedicated server or in the cloud. The Deep Security platform sends system and security event logs to this server, which forwards them securely to the Sumo Logic Data Analytics Service.
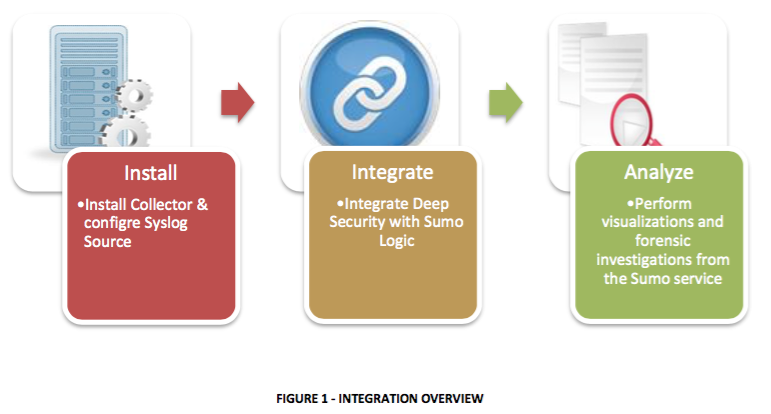
Figure 1 provides a high-level overview of the integration process.
III. INSTALL DATA COLLECTOR
Install Options
The first thing to consider when you set up the integration is how to collect data from your Deep Security deployment and forward it to Sumo Logic. There are three basic methods available, local host data collection, centralized syslog data collection and hosted collector.
Deep Security uses an installed centralized collector with syslog source. In this method, an installed Collector with Syslog Sources can be used to collect all relevant data in a centralized location before forwarding it on to Sumo Logic’s cloud-based service.
Installed Collector with Syslog Sources
The installation process involves the deployment of a Sumo Logic collector in your environment and then adding a Syslog Source to it. A Sumo Logic Installed Collector can be installed on any standard server and used to collect local files, remote files or to aggregate logs from network services via syslog. You can choose to install a small number of collectors to minimize maintenance or you can choose to install many Collectors on many machines to leverage existing configuration management and automation tools like Puppet or Chef.
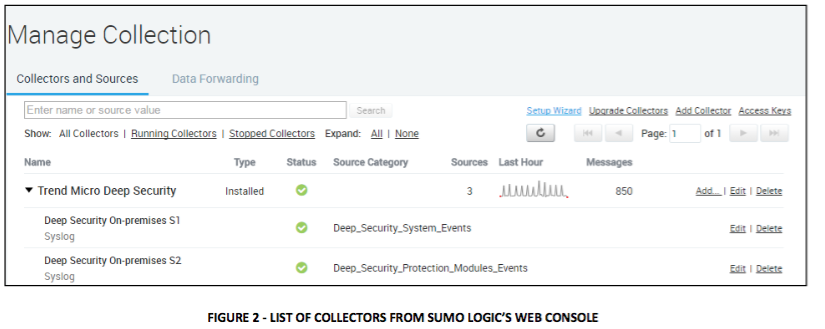
At the minimum you will need one “Installed Collector” setup for Deep Security. The number of syslog sources you need depends on the types of event logs that you are sending to Sumo logic. You will need one syslog source for each type of event. There are two types of events in Deep Security: “System Events” and “Security Events”.
In the example shown below, we have configured Sumo Logic Installed Collector with two Syslog Sources using UDP protocol.
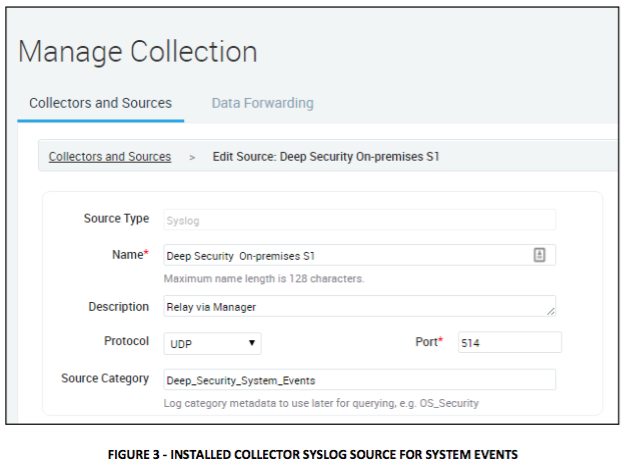
In this example setup, the first syslog source is listening on UDP port 514 for System Event Log forwarding.
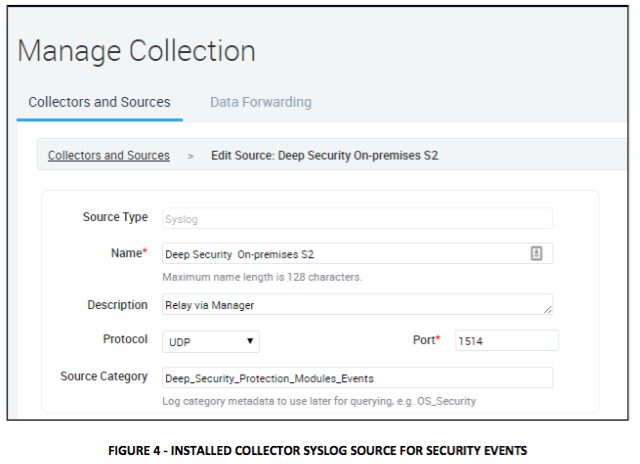
The second syslog source below is listening on UDP port 1514 for Security modules event log forwarding.
IV. INTEGRATE WITH SUMO LOGIC
System Event Log Forwarding
The integration of Trend Micro Deep Security for system events forwarding to Sumo Logic is done via system setting (Administration System Settings SIEM) configuration as shown below:
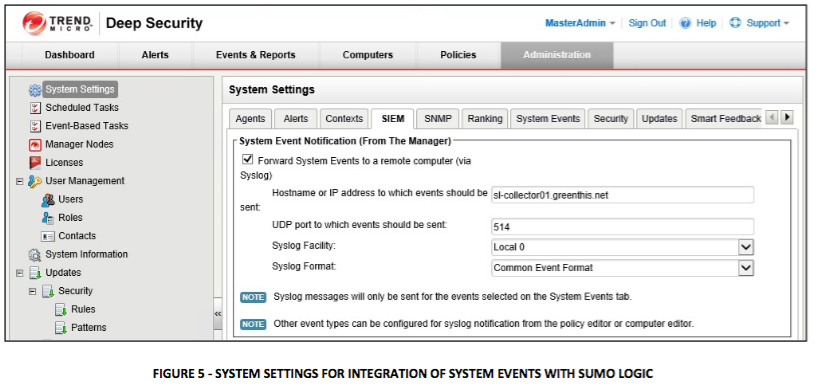
Security Event Log Forwarding
The integration of Trend Micro Deep Security for security event forwarding to Sumo Logic is done via Policy configuration and requires a Syslog Source with UDP protocol and connection information to be added to the policy. Deep Security allows Policy inheritance where child policies inherit their settings from their parent Policies. This way you can create a policy tree that begins with a top/base parent policy configured with settings and rules that will apply to all computers.
When you have a single collector installed in your environment to collect logs from Deep Security it is recommended to set the integration details at the Top (root/base) policy as shown below:
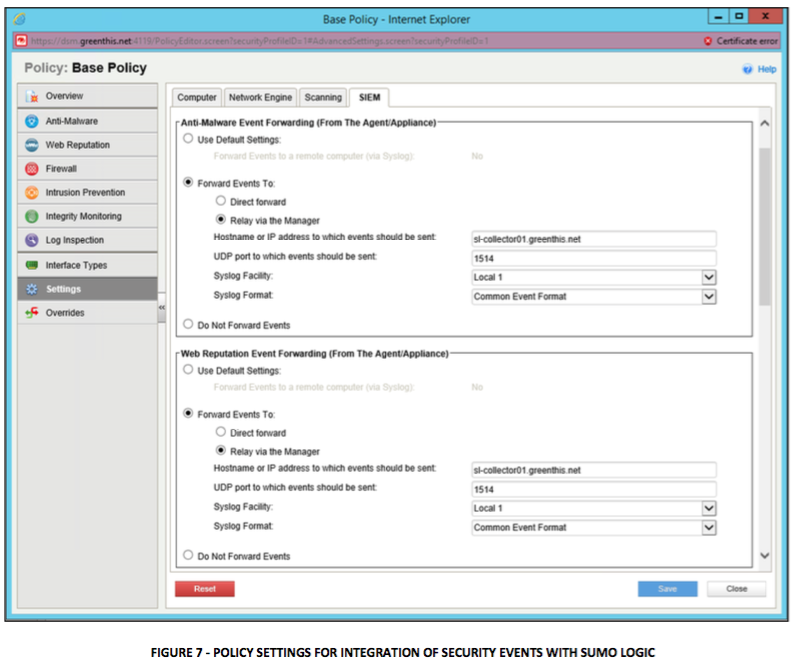
Additionally, you can configure individual collectors for each security protection module or have all Deep Security modules to send logs to one collector depending on your requirements.
Integration Options for Security Events Logs
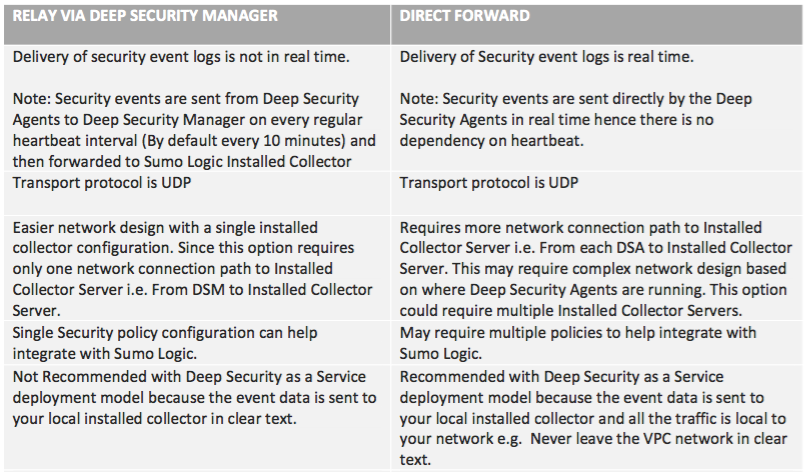
There are two integration options available to configure Deep Security Solution to forward security events to Sumo Logic, Relay via Deep Security Manager and Direct Forward.
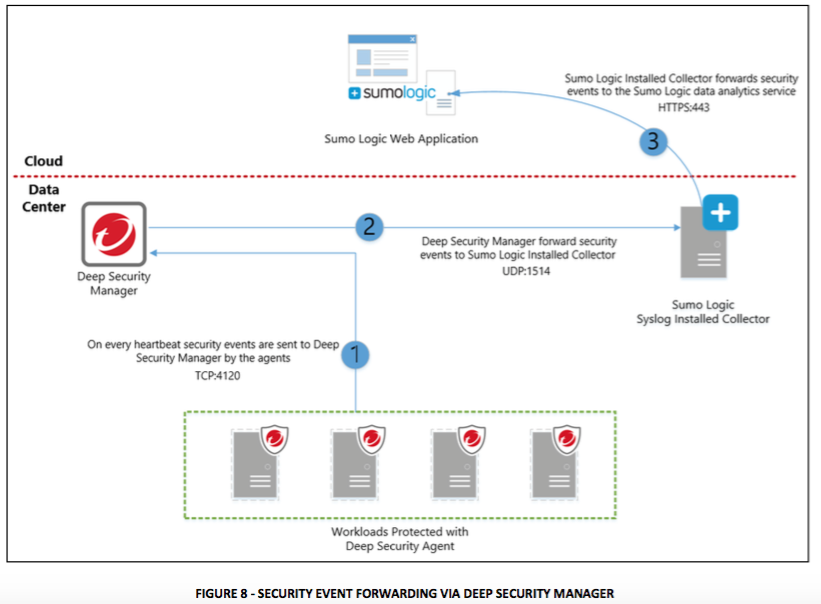
Relay via Deep Security Manager
This option sends the syslog messages from the Deep Security Manager after events are collected on heartbeats as shown below:
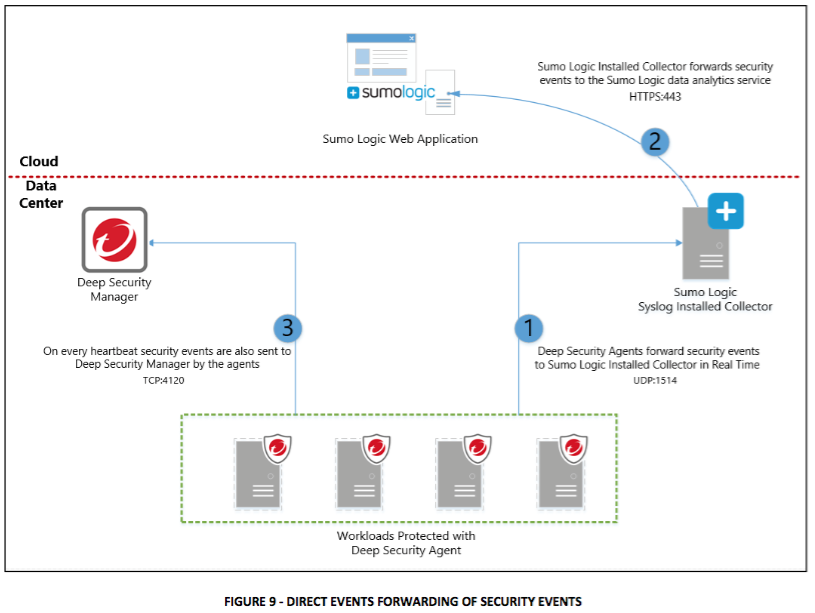
Direct Forward from Deep Security Agents
This option sends the security events/messages in real time directly from the Agents as shown below:
Comparison Between the Two Integration Options
When you are deciding what integration option to choose from to send security events to Sumo Logic Installed Collectors among these two integration choices, consider your deep security deployment (as a Service, AWS and Azure Marketplace AMI/VM or software), your network topology/design, your available bandwidth, and deep security policy design. The table below provides comparison between these two choices for easier decision process:
V. ANALYZE EVENTS LOGS
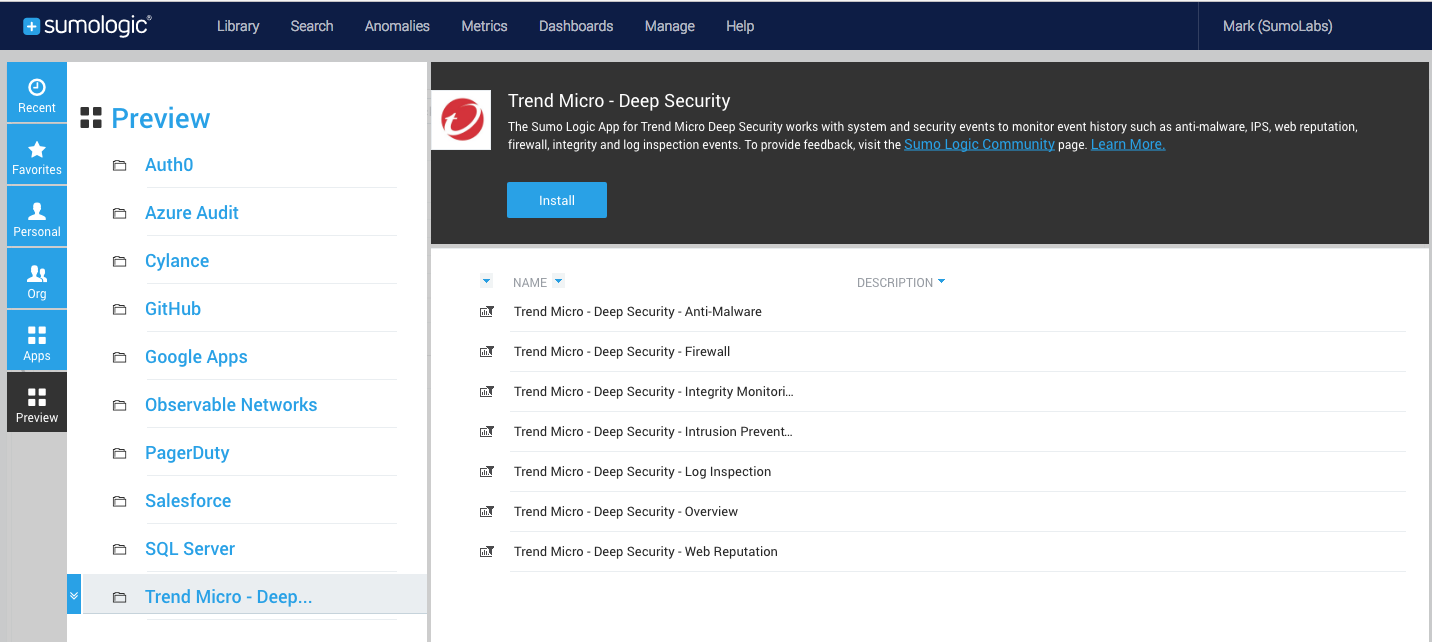
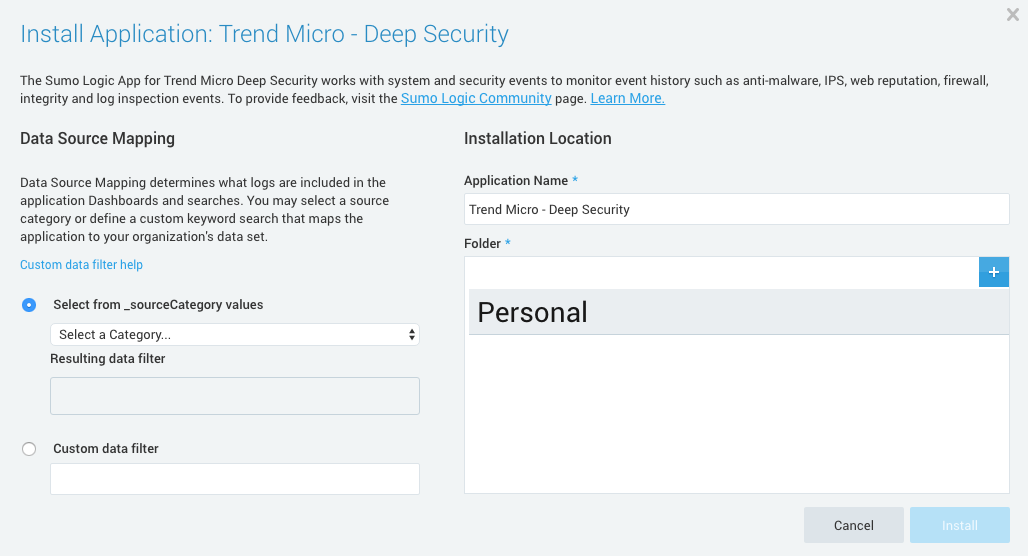
Once the install and integration steps are done, you are almost set to analyze Deep Security event data in Sumo Logic. Log into the Sumo Logic console, jump down to the preview tab section, and select “install” under Trend Micro – Deep Security. Once you define the _sourceCategory, you are set to run searches, identify anomalies and correlate events across your protected workloads. You can also leverage out-of-the-box, powerful dashboards to unify, enrich and visualize security related information across your entire physical, virtual and cloud infrastructure.
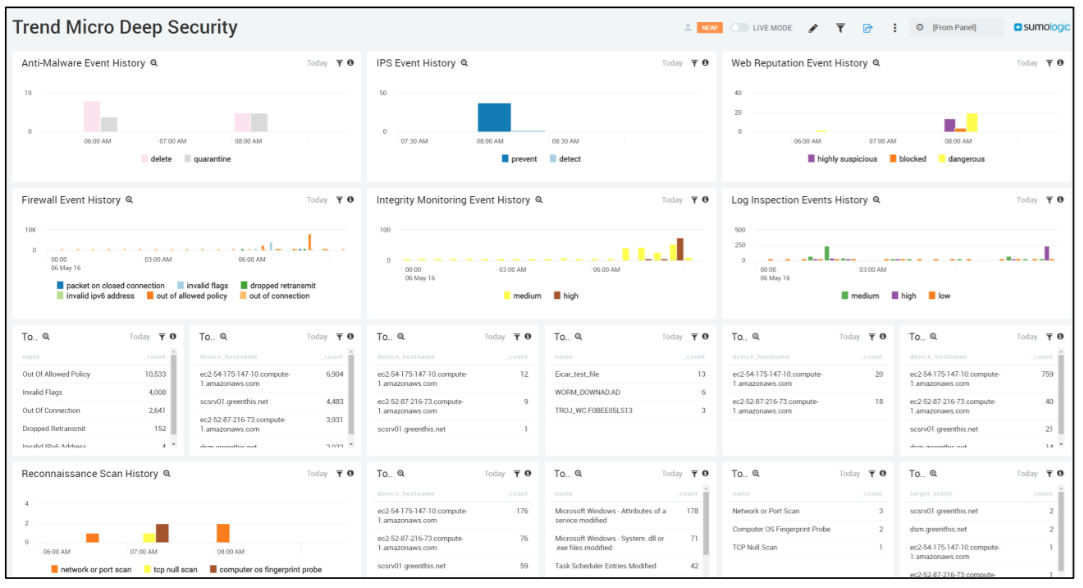
Sumo Logic Dashboard
The Sumo Logic dashboards are a powerful visualization tool to help accelerate the time to identify anomalies and indicators of compromise (IOC). The saved searches powering these dashboards can also be leverage for forensic investigations and to reduce the time it takes for root cause analysis and remediation. The uses for Dashboards are nearly endless. Perhaps your IT security group wants to keep an eye on who is installing virtual machines.
You can edit, create and save the queries you run as a panel in a Dashboard, and watch for spikes over time in a line graph. Multiple graphical options/formats are supported. Dashboards bring additional assurance, knowing that unusual activity will be displayed real time in an easy-to-digest graphical format. The data that matters the most to you is even easier to track.
How to Learn More on Security
For additional learning on Trend Micro Deep Security, please visit their site.
To watch a video from Infor’s CISO, Jim Hoover, on how to securely scale teams, manage AWS workloads and address budget challenges, please watch here.
*A special thanks to Saif Chaudhry, Principle Architect at Trend Micro and Dwayne Hoover , Sr. Sales Engineering Manager at Sumo Logic for making this integration and App a reality!



