Security concerns and skill shortages continue to impede cloud adoption
Migration to the cloud is still being hampered by the security concerns this new frontier poses to these organizations and due to the same cybersecurity skills gaps already present in many if not most of these organizations today. This was highlighted in a 2017 survey by Forbes where 49% of respondents stated that they were delaying cloud deployment due to a cyber security skills gap. And even with adequate staffing, those organizations who have adopted some facet of cloud into their organization, express concerns in their abilities to monitor and manage these new environments.
Sumo Logic and Amazon GuardDuty to the rescue
Sumo Logic was founded over seven years ago, by security industry professionals, as a secure, cloud-native, machine data analytics platform, to convert machine data into real-time continuous intelligence, providing organizations with the full-stack visibility, analytics and insights they need to build, run and secure their modern applications and cloud infrastructures.
The Sumo Logic platform provides security analytics and visibility across the entire AWS environment with context derived from details such as user access, platform configurations, changes, and with the ability to generate audit trails to demonstrate compliance with industry standards. Sumo Logic also correlates analytics from Crowdstrike threat intelligence to identify risks and threats in the AWS environment such as communications with malicious IPs, URLs, or Domains.
At AWS’ annual re:Invent 2017 conference in Las Vegas this week, they announced the availability of Amazon GuardDuty. GuardDuty, provides AWS users with a continuous security monitoring and threat detection service. And due to Sumo Logic’s strong, and long standing relationship with AWS, Sumo Logic was provided early access to the beta version of GuardDuty, which allowed the team to develop, announce and release in parallel with Amazon, the complimentary Sumo Logic Amazon GuardDuty App.
The way GuardDuty works is by gathering log data from three distinct areas of the AWS cloud environment including:
- AWS Virtual Private Cloud (VPC) “flow logs”
- AWS CloudTrail “event logs”
- AWS Route 53 DNS “query logs”
Along with the log data above, AWS provides additional sources of context (including threat intel associated with the AWS environment) to provide users with identification of potential threats in their environments. These potential threats are called “findings” by GuardDuty. Each “finding” provides users with details about each of the threats identified so that they can take any necessary action as needed.
“Findings” details include to following information:
-
- Last seen – the time at which the activity took place that prompted the finding.
- Count – the number of times the finding was generated.
- Severity – the severity level (High, Medium, or Low)
- High – recommendation to take immediate remediation steps.
- Medium – investigate the implicated resource at your earliest convenience.
- Low – suspicious or malicious activity blocked. No immediate action needed.
- Finding Type – details and include the:
- Threat Purpose (more details available in the GuardDuty User Guide):
-
-
- Backdoor
- Behavior
- Cryptocurrency
- Pentest
- Recon
- Stealth
- Trojan
- UnauthorizedAccess
-
-
- Resource Type Affected: with the initial release of GuardDuty “only EC2 instances and IAM users (and their credentials) can be identified in findings as affected resources”
- Threat Family Name: the overall threat or potential malicious activity detected.
- Threat Family Variant: the specific variant of the Threat Family detected.
- Artifact: a specific resource owned by a tool used in the attack.
- Region – the region in which the finding was generated.
- Account ID – the ID of the AWS account in which the activity took place t
- Resource ID – the ID of the AWS resource against which the activity took place
- Target – the area of your AWS infrastructure where GuardDuty detected potentially malicious or anomalous activity
- Action – the activity that GuardDuty perceived to be potentially malicious or anomalous.
- Actor – the user that engaged in the potentially malicious or unexpected activity
The Sumo Logic Amazon GuardDuty App Value-Add
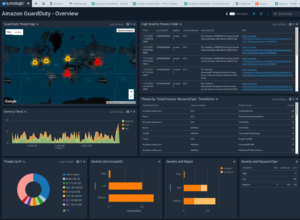
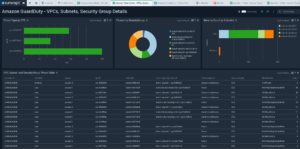
Pre-built Sumo Logic GuardDuty dashboards: Sumo Logic provides a single pane of glass to reduce the complexity of managing multiple environments, with pre-configured, user friendly and customizable dashboards that take GuardDuty’s linear data format and layers-on rich graphical reporting and depictions of trends over time.
Click to Fix: The Sumo Logic Amazon GuardDuty App allows users to rapidly, and visually identify “findings”, ranked by their severity levels (high, medium, and low), and can simply click on any of them to be automatically routed to their AWS environment to take any necessary actions for remediation.
Value-added Context: The Sumo Logic Amazon GuardDuty App adds additional sources of analytics for deeper and wider visibility in the AWS environment and context across the organization including full stack visibility into application/infra logs, Application/Elastic Load Balancer (ALB/ELB) performance, and supplemental threat intel provided by Crowdstrike with no additional fees.
The new Amazon GuardDuty offering along with capabilities from Sumo Logic’s tightly integrated GuardDuty App provides organizations with the tools they need to more simply and effectively manage and monitor their AWS cloud environments. And with the visibility for more rapid detection and remediation of real and potential threats to mission critical resources in those environments.